Overview
This guide follows the standard
ssh-audit hardening guide,
tweaked for Alpine Linux.
Hardening Guide
These steps must be performed as root. You can try to use doas or sudo, but
there may be issues.
- Re-generate the RSA and ED25519 keys
rm /etc/ssh/ssh_host_*
ssh-keygen -t rsa -b 4096 -f /etc/ssh/ssh_host_rsa_key -N ""
ssh-keygen -t ed25519 -f /etc/ssh/ssh_host_ed25519_key -N ""
- Remove small Diffie-Hellman moduli
awk '$5 >= 3071' /etc/ssh/moduli > /etc/ssh/moduli.safe
mv /etc/ssh/moduli.safe /etc/ssh/moduli
- Enable the RSA and ED25519 HostKey directives in the /etc/ssh/sshd~config~
file
sed -i 's/^\#HostKey \/etc\/ssh\/ssh_host_\(rsa\|ed25519\)_key$/HostKey \/etc\/ssh\/ssh_host_\1_key/g' /etc/ssh/sshd_config
- Restrict supported key exchange, cipher, and MAC algorithms
echo -e "\n# Restrict key exchange, cipher, and MAC algorithms, as per sshaudit.com\n# hardening guide.\nKexAlgorithms [email protected],curve25519-sha256,[email protected],diffie-hellman-group16-sha512,diffie-hellman-group18-sha512,diffie-hellman-group-exchange-sha256\nCiphers [email protected],[email protected],[email protected],aes256-ctr,aes192-ctr,aes128-ctr\nMACs [email protected],[email protected],[email protected]\nHostKeyAlgorithms ssh-ed25519,[email protected],[email protected],[email protected],rsa-sha2-512,[email protected],rsa-sha2-256,[email protected]" > /etc/ssh/sshd_config.d/ssh-audit_hardening.conf
- Include the /etc/ssh/sshd~config~.d directory
echo -e "Include /etc/ssh/sshd_config.d/*.conf" > /etc/ssh/sshd_config
- Restart OpenSSH server
rc-service sshd restart
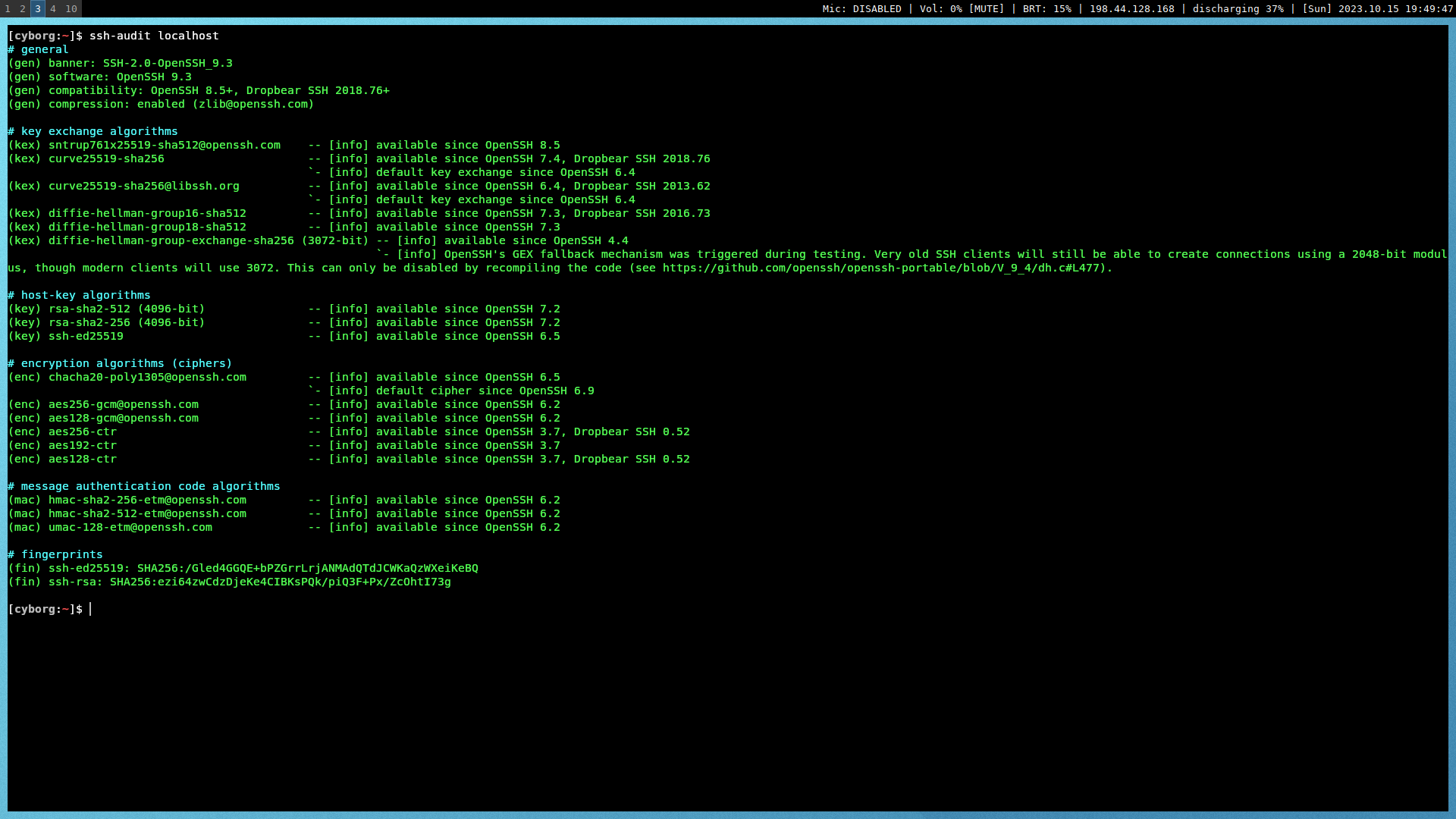
Testing SSH
You can test the results with the ssh-audit python script.
pip3 install ssh-audit
ssh-audit localhost
If everything succeeded, the results will show as all green. If anything is
yellow, orange, or red, you may need to tweak additional settings.
#+caption: ssh audit